Wordfence has reported a phishing campaign targeting WordPress users with an email claiming to be from the WordPress team and warning of a remote code execution vulnerability with the identifier CVE-2023-45124. However, this identifier is not a valid CVE. The email prompts the victim to download and install a “Patch” plugin.
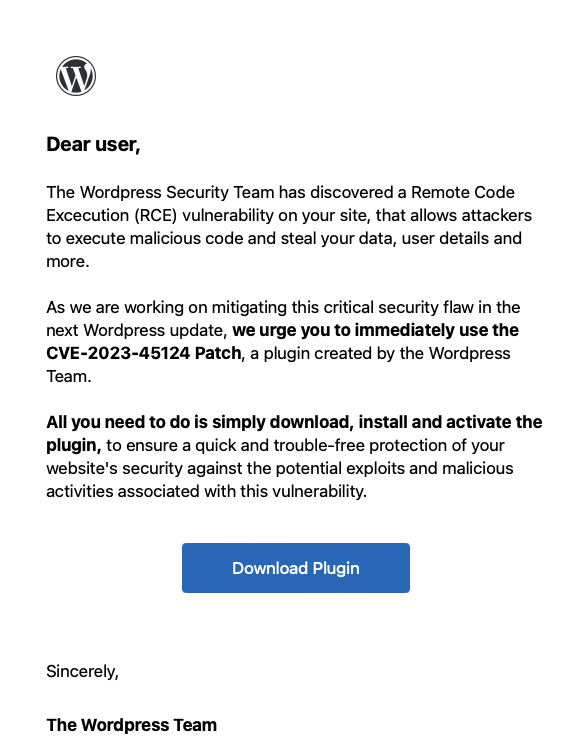
but instead, it redirects victims to a convincing fake landing page at en-gb-wordpress[.]org. It is recommended to be cautious and not download or install any suspicious plugins.
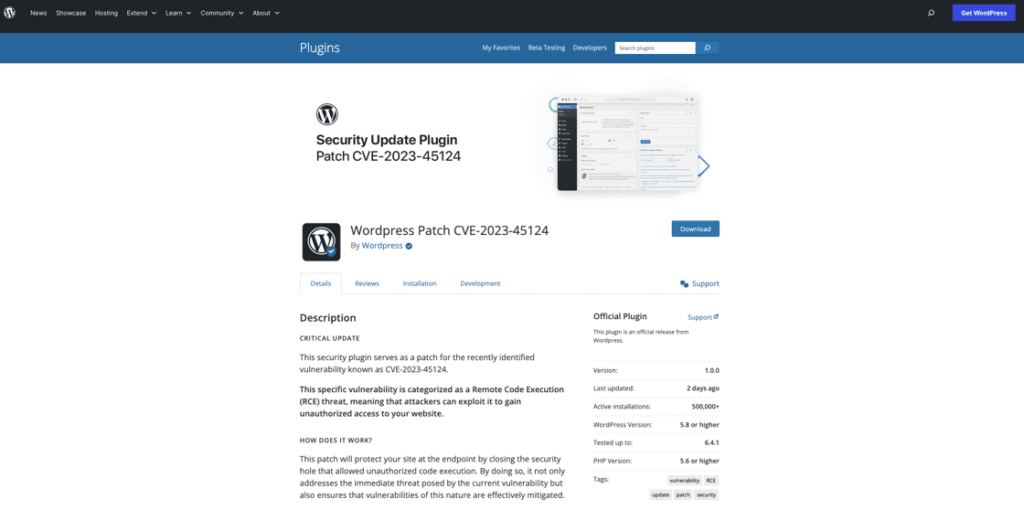
The plugin, disguised as a security update, is installed with a slug of “wpress-security-wordpress” and adds a malicious administrator user with the username “wpsecuritypatch”. The plugin sends the site URL and generated password for this user back to a C2 domain, wpgate[.]zip. Additionally, the plugin downloads a separate backdoor, wp-autoload.php, from the C2 domain and saves it in the webroot. This backdoor includes a hardcoded password and provides a file manager, SQL client, PHP console, and command line terminal, as well as displaying server environment information.
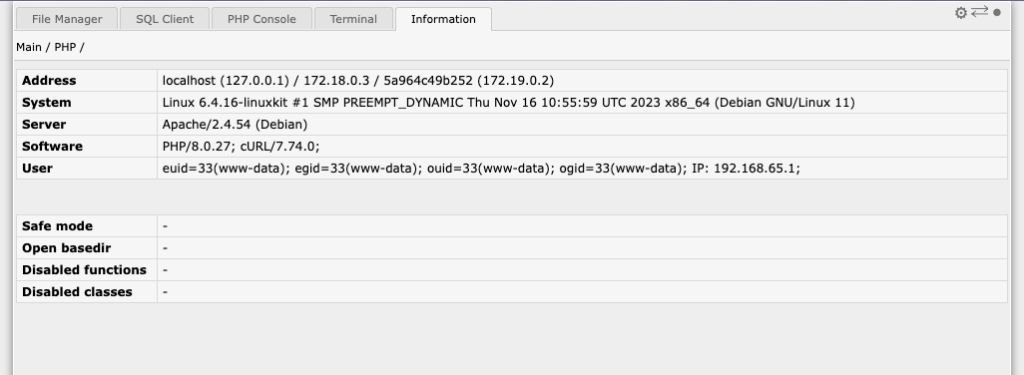
This vulnerability allows attackers to maintain access to the WordPress site and server even after a successful login attempt. This can lead to full control over the site and server, posing a significant security risk.
Source: wordfence
