When the coronavirus threatens to become a global pandemic, everyone is paying close attention because it is spreading throughout the world. But now the virus has become an advantage to the hackers because they have found a way to use this board to inject malware into computers.
reason Cybersecurity recently released a threat analysis report describing new attacks that are taking advantage of the increasing desire of Internet users for information about the new coronavirus that is causing global chaos.
The attacker created a website related to the coronavirus to ask you to download the application to keep up with the situation. This application does not require installation and shows you the COVID-19 distribution card. However, this is a place for attackers to produce dangerous binary files and install them on your computer.
To be very clear, this website is a real coronavirus tracking map but has a different URL or details from the original source.
At present, the malware only affects Windows computers. However, Alfasi expects attackers to work on new versions that can affect other systems.
Signs of Infection
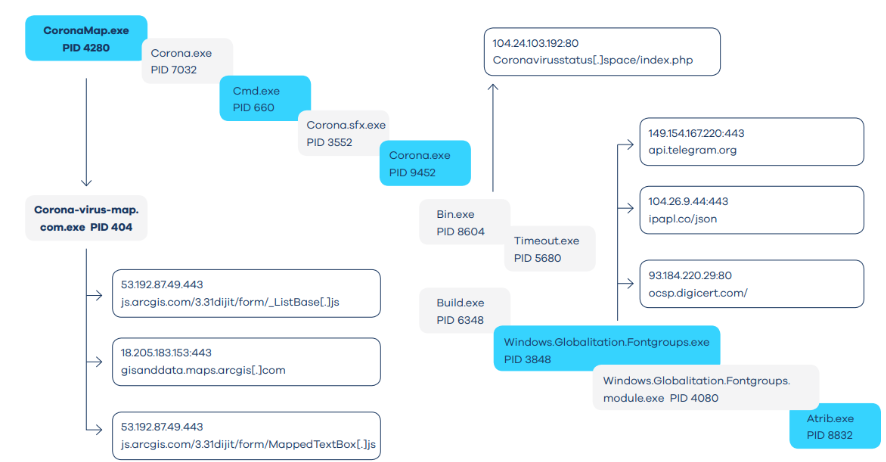
Running Corona-virus-Map.com.exe duplicates the Corona-virus-Map.com.exe file and some Corona.exe, Bin.exe, Build.exe, and Windows.Globalization.Fontgroups. Exe file
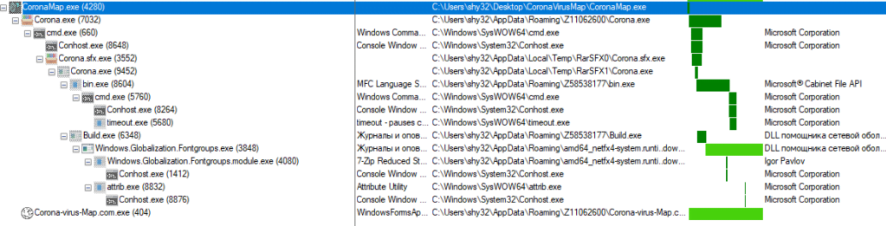
In addition, the malware changes several registers in ZoneMap and LanguageList. Some mutex is also made.
Malware implementation allows the following processes: Bin.exe, Windows.Globalization.Fontgroups.exe, and Corona-virus-Map.com.exe. These attempt to connect to several URLs.
This process and URL are just one example of an attack. Many other files are generated and the process starts. They make different network communication activities when malware tries to collect various types of information.
How CoronaVirus Map Steals Information
Alfasi presents a detailed report on how he dissected malware in a blog post on Reason Security. One of the main details is his analysis of the Bin.exe process using Ollydbg. Thus, the process has written several DLL (Dynamic Link Libraries). DLL “nss3.dll” caught his attention because he was realized by various actors
Alfasi monitors the static loading of the API associated with nss3.dll. This API seems to make it easier to decrypt saved passwords and produce output.
This is a common approach by data thieves. Simply put, it only collects credentials from the infected web browser and moves it to the C: \ Windows \ Temp folder. This is one of the hallmarks of AZORult attacks, where malware extracts data, generates unique IDs on infected computers, uses XOR encryption and then starts C2 communication.
The malware makes certain calls to steal credentials from regular online accounts such as Telegram and Steam.
malware execution is the only step needed to continue information theft. Victims may not interact with or enter sensitive information in the window.
Prevention
To prevent this malware you need to install the Reason Antivirus software. because Reason is the first to find and scrutinize this new threat, so they can handle it effectively. Other security companies might have heard about threats when Reason went public on March 9. Your antivirus or anti-malware tool will be updated at the time of publication.

